Archive for July, 2007
Sacrifice my morals, or work for Primerica
 It is now 6:49:21pm on a Sunday night. I am sitting at home on the couch, writing up some code for my Wikipedia projects when I receive a call on my mobile phone, from a local number in the 860 area code.
It is now 6:49:21pm on a Sunday night. I am sitting at home on the couch, writing up some code for my Wikipedia projects when I receive a call on my mobile phone, from a local number in the 860 area code.
The nice woman tells me she’s found my resume online and thinks I’d be interested in a position she has.
She then tells me she is from “..a division of CITI Group”. She asks me if I’m still looking for work. I tell her that I am still actively considering positions. Then she asks me…
“..do you ever consider doing something unlike anything you’ve ever done before.”
I say “Sure, every day.”
Then she restates that she’s is from “…a division of CITI Group, a major financial services group”, and asks me if I’d like to hear more. I say “Yes, go on…” and then she says she works for a company called “Primerica”.
I think to myself… “Primerica… Primerica… I’ve heard that name before.”
DING! Primerica is an MLM company!
So I ask her…
“If this opportunity has anything to do with Sales, Marketing or Direct Marketing… I’m sorry, but I’m not interested.”
She said something very nice in return, even though I just killed her referral bonus right there. She said something like “I guess we conclude our call here. Good luck in the future.” and I said the same.
CLICK!
A quick Google revealed this post that has some detailed information on the scam:
There will always be a huge drop out rate and while you may have made a $100,000 by recruiting x amount of people… it’s really cheap change compared to the money Primerica made off of you and it’s short term money in that eventually you won’t be able to find new recruits and/or new people to sign up for their finanical programs.
So what happens at this point is the pyramid collapses bottom up and eventually you will find yourself having no recruits to capitalize on and be forced to drop out yourself.
A refreshing view from a refreshing candidate, Ron Paul
If you’re sick of the standard Doublespeak rhetoric from the Republicans and Democrats currently coming to the center in the current administration, take a listen to Ron Paul’s speeches.
I’m looking for a candidate that supports what the Constitution says, NOT what they THINK the Constitution says.
Let’s get back to the way we’re supposed to be running this country. The current front-runners in the 2008 campaign are not getting my vote, because they haven’t expressed that they’ll support my personal views, or the views of the rest of the country.
Ron Paul so far, seems to be the closest one to my personal views from what I’ve seen and read so far.
Squid + Privoxy + Tor for secure, transparent web browsing
With the advent of the new illegal monitoring going on in the USA, and ISPs being actively forced to log and snoop on their own customer’s behaviors, I’ve been advocating the use of Privoxy + Tor to help anonymize some of your browsing behavior and characteristics.
Privoxy is a web proxy with advanced filtering capabilities for protecting privacy, modifying web page data, managing cookies, controlling access, and removing ads, banners, pop-ups and other obnoxious Internet junk.
Tor is a toolset for a wide range of organizations and people that want to improve their safety and security on the Internet. Using Tor can help you anonymize web browsing and publishing, instant messaging, IRC, SSH, and other applications that use the TCP protocol.
To configure them to work in concert, just install privoxy and tor using your standard package management tools. Open up Privoxy’s configuration file (normally /etc/privoxy/config) and add the following line:
forward-socks4a / localhost:9050 .
The ending dot is significant, don’t forget to include it. You can put this anywhere in the file you want, but the most-likely place is around line 1064 or so in the standard configuration. Restart privoxy using whatever scripts or service management tools your host operating system provides.
Now there’s an additional tweak you can do to use Squid to pool and cache the sites you visit locally. To do that, you’ll need to change a few things in Squid’s configuration (normally /etc/squid/squid.conf):
http_port 8888 cache_peer localhost parent 8118 7 no-query default # Some basic ACLs to allow local traffic, forbid outside traffic http_access allow purge localhost http_access allow localhost http_access deny all # Make sure we're ALWAYS using Privoxy and Tor, and not bypassing the cache never_direct allow all # And let's remove some headers which can be used to divulge some of our personal info header_access From deny all header_access Server deny all header_access User-Agent deny all header_access WWW-Authenticate deny all header_access Link deny all
Restart Squid and you should be all set. In your application (for example, Firefox), you can set up your proxy server to be:
localhost:8888
Browsing will be slightly slower, but very clean and anonymized. If you want, you can also run pre-fetch pages with Squid to speed up access to lateral pages and links on sites you visit.
Using Firefox, I have an extension called SwitchProxy installed which lets me change my proxy configuration with a simple click, from “None” to “Squid (localhost)” to “Squid + Privoxy + Tor”, and so on. I highly recommend it.
In my personal configuration, I have a router which is configured to send every outbound request on port 80, and every incoming reply, to a Squid server running on FreeBSD. No client configuration is necessary at all.
With Squid on the BSD machine, I can set up Privoxy and Tor there, and transparently cache, secure, and anonymize that traffic without burdening the clients at all, no matter how many there are, or what OS they happen to run.
My router’s iptables configuration for that looks like this:
iptables -t nat -A PREROUTING -i br0 -s ! 10.0.1.3 -p tcp --dport 80 -j DNAT --to 10.0.1.3:8888 iptables -t nat -A POSTROUTING -o br0 -s 10.0.1.0/24 -d 10.0.1.3 -j SNAT --to 10.0.1.1 iptables -A FORWARD -s 10.0.1.0/24 -d 10.0.1.3 -i br0 -o br0 -p tcp --dport 8888 -j ACCEPT
10.0.1.1 is my router, and 10.0.1.3 happens to be the FreeBSD machine running a very large Squid cache.
It works great, and clients behind my LAN never know the difference.
If you’re afraid of The Oracle taking too much of your personal browsing history for their own purposes, you can install the CustomizeGoogle extension and filter some of that out.
CustomizeGoogle lets you anonymize your Google UserID, filter out spammy websites, block Google Analytics cookies, and much more.
dspam Hackery 101, converting messages to mbox

I’ve been running dspam for many years here at gnu-designs, inc. We replaced SpamAssassin with it several years ago, because SA was just not getting any better at filtering spam away from user’s mailboxes.
After a few weeks of using dspam, our filtering performance was over 95%, and rising steadily. 3 years later, we weren’t seeing a single spam slip through to any user’s mailbox. It was very impressive.
Later, I added graymilter in front of dspam to thwart off even more spam. You can see the difference it made:
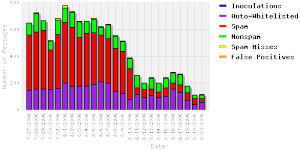
After a few years, Jonathan A. Zdiarski (author/maintainer of dspam) sold the dspam project to Sensory Networks, and it still continues to be updated on a regular basis today.
But there’s one thing that has always bugged me about dspam… the catchall for messages is stored in $DSPAM_HOME/dspam.messages, and it contains a concatenated list of all messages processed by dspam.
So far, so good… until you need to retrieve one back out of there.
The file is actually a literal concatenation of every message. With the amount of mail we receive, that file grows very large, very fast. I stumbled across a bug today with dspam where messages in the web interface were just vanishing after being forwarded back into the user’s mailbox as non-spam. I needed a way to go back in and retrieve the messages.
Enter the Swiss-Army Chainsaw again; Perl!
With a simple perl one-liner, I was able to turn this “useless text file” of concatenated messages into an mbox-format file I could load up in pine and read like a normal mailbox. From there, I could forward the false-positives back to the users, when the webui eats them for lunch. It looks like this:
perl -pi.$$ -e '$time=scalar(gmtime); s,^(Return-Path: .*)$,From dspam $time\n$1,g' dspam.messages
In simple terms, all this does is take the “Return-Path” line that appears at the start of each message, and pre-pends the “From ” line on the line right before it. Note that this is the “From ” (space after) line, not the “From:” (colon after) line. They are different.
That’s it. Now I can just do:
pine -f $DSPAM_HOME/dspam.messages -i
And away we go!
I’ll end up patching the source to produce this output at some point, but for now, this solved an immediate need I had to fix a critical problem.
I love dspam for what it does. The installation is not for the feint of heart, but after you get it set up, what it does is pure magic, and your users will love you for it. The web interface removes the bulk of the work of maintaining whitelists, filtering scores and other things, and delegates it to each user, where they can customize their own filtering however they choose.

Jonathan also wrote a book on dspam and filtering, and I highly recommend picking up a copy if you can.
We no longer pass laws, we sign Executive Orders
Its no surprise that the current Administration has taken it upon itself to continue to break the law in hundreds of ways and disassemble the oversight committees that are there to ensure those laws are enforced, but now we’ve reached a new low.

We no longer have to pass laws. Those pesky laws are always getting in the way of the real goal: A totalitarian, police state. We can’t have those annoying checks and balances getting involved here. We can’t get anything done, if they keep shooting down our great ideas!
So now we just sign Executive Orders instead. Without judicial oversight, no way to contradict the orders, they just get passed, and that is that.
Don’t continue to fall for this abuse of our way of life, a way of life our forefathers died to uphold and protect!
There are four boxes to use in the defense of liberty: soap, ballot, jury and ammo. Use in that order. Starting now.
But wait, there’s more about Cheney
Moments after I posted the last entry about Cheney claiming he’s not a part of the Executive Branch of government, and therefore not subject to the subpoenas, I found this interesting story that hints at Cheney about to invoke Executive Privilege to keep his secrets, well… secret.

I’m sorry Dick, you can’t have it both ways. Either you are a member of the Executive Branch of government, and subject to the subpoenas, or you are not, and you cannot invoke Executive Privilege.
Every day, this government gets more and more unstable. Are we seeing the beginnings of Newspeak here?
Cheney is not part of the Executive Branch
Well, its a good thing that Vice President Cheney is not a member of the Executive Branch of government any longer. He’s decided to absolve himself of that responsibility.

This means that if President George W. Bush meets an unfortunate or untimely end, Dick Cheney (as a non-member of the Executive Branch) does not automatically become President of the United States.
Whew!
Because a man (and I use that term very loosely in this case) who can shoot a man in the face and get that same man to apologize for the “pain and suffering he caused Cheney and his family”, or who has man-sized safes in his office for the purposes of hiding/destroying more “secret” material, shouldn’t be allowed to go NEAR the government’s inner workings.
We’re heading down a fast slippery slope here… and so I’ll lay out the same prediction I’ve been stating for the last 3+ years. Originally I thought we’d have a civil war when Bush stole the seat of President in the 2004 election, but the American public just sat back and let it happen; content to watch American Idol, wear their Nike shoes and drink their Pepsi colas.
This time, I don’t think it is going to go down so lightly. People who are this entrenched in Government, this wrapped in their own mindless games for power, do not just walk away when their term is up.

Prediction Follows:
George W. Bush is going to “temporarily suspend” (read: permanently) the 2008 elections, because of the “War in Iran” (note: not Iraq). Martial Law will be implemented shortly after, to try to calm people from creating a general uprising.
Those that refuse to be “calmed” (read: controlled, suppressed), will be added to the list of those being illegally wiretapped by the NSA. This wiretapping has been happening in our country for over 5 years before it became public. You can bet they’re building a list right now of the “dissidents” who might cause problems in 2008 for their stealing of the elections.
We can’t have those “un-American peoples” rising up against their government, now can we?
Let’s also not forget that Michael Hayden directly misrepresented the 4th Amendment in a press conference. It is very clear, this Administration doesn’t understand what they’re doing, they’re a direct threat to the Freedom and Democracy of this country and others, and they should be replaced immediately, by those more-suited to handling this country’s issues and problems.
End Prediction
We CAN, and we should rise up against the government when they are a threat to our own way of life. They’re not called “un-Americans”, they’re called Patriots, and this administration (and the next), better get used to hearing and seeing that term more and more.
Watts-Up with my power?
 I recently purchased a WATTS-UP Pro power analyzer/data logger from SMARTHOME in an effort to try to ascertain how much power my home and office equipment was consuming on a monthly basis.
I recently purchased a WATTS-UP Pro power analyzer/data logger from SMARTHOME in an effort to try to ascertain how much power my home and office equipment was consuming on a monthly basis.
We’re currently paying roughly $180/month for the power we use. At 0.12kWh, that’s a lot of power we’re consuming SOMEWHERE. Where is it?
What is taking up the most power?
Is it the computers?
Is it the appliances?
Is it something else?
We’ve already replaced every conventional incandescent bulb with compact fluorescent lamps, which are saving about 80% of the power right off the top from the bulbs we were using before. But it isn’t enough to bring the monthly bill down to make a difference.
I started testing my office, various appliances, outlets, other things. What I found, was shocking and surprising. Here’s a small sample:
My Gateway FPD2485W 24″ LCD monitor consumes 90 watts(!!) of power while turned on. It was the single-highest power eater I tested so far.
This monitor is plugged into a 16-outlet strip, which also includes an AMD64/4600+ machine with 4gb RAM, several USB gadgets, bluetooth adapters, phone charger, flatbed scanner, rechargeable battery charger, landline phone extension and several other things.
The total consumption of all of those devices, is 282W total. The LCD is eating 30% of everything else. The AMD64 machine itself consumes 100W.
The TV/DVR/Stereo takes 140W, and is on 24×7.
A 3-speed fan in my office takes 250W on the fastest setting.
The dehumidifier I use in my office is a 600W device, and after spinning up, it eats 687W. Unfortunately, the dehumidifier is a necessary device in the office, otherwise I’d have my own weather system in there in 3 days. I pull about 3 gallons of water out of the air every day in the office.
The toaster oven in the kitchen cooking 2 slices of toast on the “Toast” setting: 1300 WATTS!!!
I’ve only had it for a few hours, but the results are quite shocking and surprising so far. I’m going to start testing under load, over longer periods and on the bigger usage appliances (washer, dryer, refridgerator and such).
So many iTunes iProblems and iBugs
Tags: Apple, iTunes, music, Windows
My wife and I have amassed a very large collection of music over the years from our CDs. I’ve painstakingly ripped all of the CDs to Ogg Vorbis format and mp3 format. There’s rougly 10,000 files on the Music slice of the FreeBSD media array I’ve built for this purpose. It’s big.
She has a 20″ iMac that I bought for her last Christmas and I have several Linux machines and one Windows machine. The Windows machine runs iTunes, while the Linux machines all run AmaroK (which blows iTunes out of the water in functionality and intuitive features).
The Windows machine has an M:\ drive mapped to the Music share on the FreeBSD server via Samba. From here, I can load iTunes and drag all of the albums into iTunes. About an hour of importing, fetching album artwork and conversion later, I have a fully populated library of music in iTunes to work with.
Almost.
The first problems began when I realized that iTunes doesn’t like having the “My Documents” folder stored on a network share (My Documents → My Music → iTunes is where iTunes stores its Music Library). if iTunes tries to launch at login time, it will barf and truncate the existing music library to create a new, empty, default music library. This means I have to reimport all 10,000 music files again.
Once I realized that, I made sure the My Documents folder was opened (initiating the network mapping) before iTunes attempts to load. Now that part works… but it is still an iTunes bug.
The second problem I found, was that iTunes doesn’t like Samba locking. The music files we have are shared on a tightly locked-down Samba share. This share looks like the following:
[Music]
comment = Music
path = /usr/local/array/Media/Music/
case sensitive = yes
writeable = yes
guest ok = no
browseable = yes
locking = yes
public = no
write list = @gnu
hide files = /.DS_Store/
Note the Bolded portion. If I have locking enabled on the Music share, iTunes won’t allow me to edit the id3v2 tags in the mp3 files. If I disable locking (NOT recommended for a multi-user share like this), then I can edit the mp3 tags, metadata and other pieces.
Why?!
Thirdly, I tried importing ALL of our music into the iTunes copy running on Windows, and then using the iTunes Sharing option to share that entire music library on the LAN, so my wife’s Mac could see and use it.
They got that wrong too.
When you share one iTunes Library, you basically create a “streaming radio station”, nothing more. This means my wife can’t plug in her iPod and pull music from the shared library to her iPod and load it up. She can only click on music and listen to it while she sits at her Mac.
No iPod functionality with iTunes music sharing. Lovely.
AmaroK 2.0 and KDE4 is soon to be released for Windows and OS X. The sooner that is done, the sooner I can be rid of this broken piece of software called iTunes on the Windows machine and on the Mac. Once we’re all on AmaroK, things will work much better.
And more voices cried out and were silenced
 There are four boxes to use in the defense of liberty: soap, ballot, jury and ammo. Use in that order. Starting now.
There are four boxes to use in the defense of liberty: soap, ballot, jury and ammo. Use in that order. Starting now.
Our failing system of democracy was dealt another blow today.. The only way to prove you were affected by the NSA wiretapping is to be affected. The fact you were affected is something you can’t prove even when you are affected because the fact that you were affected is now to remain a state secret.
Nice.
Why is it that the same exact laws the Federal Government passed when Nixon was accused of wiretapping one office are now ignored, when it comes to the unsupervised wiretapping of 280 million US Citizens?
First, Bush and the NSA denied there was any wiretapping going on. When they were caught in a lie, they immediately claimed that any information related to the non-existant wiretapping program, were state secrets.
From the article:
A divided three-judge panel for the U.S. Court of Appeals for the Sixth Circuit ruled today that the lawsuit, brought by the American Civil Liberties Union and a group of journalists, lawyers and academics, be sent back to a district court judge to be dismissed.
In August 2006, Judge Anna Diggs Taylor of the U.S. District Court for the Eastern District of Michigan ruled the NSA program, which monitored telephone and Internet communications without court-ordered warrants, was illegal.
It is at this point, I must requote the definition of Liberalism:
Broadly speaking, liberalism emphasizes individual rights and equality of opportunity. A liberal society is characterized by freedom of thought for individuals, limitations on power, the rule of law, the free exchange of ideas, a market economy, free private enterprise, and a transparent system of government in which the rights of all citizens are protected.
And from a post on Slashdot discussing this travesty:
The government no longer answers to the citizens, according the the system we set up to run it. It’s a very short, swift step from where we are to where ordinary citizens disappear in the night (non-Muslims, that is).
We won’t know exactly when that moment arrives, because we won’t be told, because no one in the government obeys or enforces the law anymore.
Another random snippet discussing this ruling:
“This stuff is so super secret that we can’t even show 8 members of Congress with top level security clearances what we are doing. The fact that we are legally mandated to advise them & we can only perform these operations under their oversight is irrelevant.”
There seems to be this misconception in the current government that they make up the laws that we follow, and they tell us what to do, and we do them. When we don’t obey, we’re seen as traitors or terrorists, and scared into submission (or those held captive, uncharged, in Guantanamo).
Let me restate, as I have many times before… this Government can, and will be replaced. There are 280 million of us, and not nearly as many of you. We’re armed, we’re strong, and when the cause it right, we WILL unite and fight for what is right.
Are you hearing this? WE are the Government, not you, and if you are not representing what WE believe to be OUR best interests, you will be voted out. If you rig the voting system (as has been done in the last two “elections”), we’ll replace you by other means.
