HOWTO: Disable Usernames from Login Managers for Linux and Windows
With all the news flying around about security, the less we give a potential malicious attacker, the better. To that end, here’s how to disable the list of usernames or the last logged-in user on your machine(s) for Windows and Linux (gdm) when you boot them up and get to the login screen.
Disable Usernames in GDM v1, v2
There are several ways to do this, some work, some do not, depending on your version of GDM (v1 vs. v2), so I’ll show you what command to run to set this, and I’ll also show you where you can set it in the actual configuration file.
If you’re running gdm (Red Hat, CentOS Fedora, Ubuntu, Debian, openSUSE), run this command:
$ sudo gconftool-2 –direct –config-source xml:readwrite:/etc/gconf/gconf.xml.defaults \ –type bool –set /apps/gdm/simple-greeter/disable_user_list true
This actually modifies the file:
/etc/gconf/gconf.xml.defaults/%gconf-tree.xml
The modifications you want to make in section “gdm/simple_greeter” are (just add/edit the whole block below):
<entry name=â€disable_user_list†mtime=â€1289993214″ type=â€schema†stype=â€bool†owner=â€gdm-simple-greeter†gettext_domain=â€gdmâ€> <local_schema locale=â€C†short_desc=â€Do not show known users in the login windowâ€> <default type=â€bool†value=â€trueâ€/> <longdesc>Set to true to disable showing known users in the login window.</longdesc> </entry>
Disable Usernames in GDM v3
If you’re using GDM3, and many current and recent Linux distributions are, here’s how to neuter the userlist so your system doesn’t leak the list of valid users who have access to the system:
Add the following to a new file you create, called 01-settings in /etc/dconf/db/gdm.d/. Make sure the text on the ‘banner-message-text’ line is all on one line in the configuration file. I’ve wrapped it here for visibility:
$ sudo vi /etc/dconf/db/gdm.d/01-settings
[org/gnome/login-screen]
banner-message-enable=true
banner-message-text='WARNING!!! You have accessed a private system.\n
UNAUTHORIZED ACCESS IS PROHIBITED\n
Violators will be prosecuted to the full extent of the law.\n
Your access to this network may be monitored and recorded for quality\n
assurance, security, performance, and maintenance purposes.'
disable-restart-buttons=true
disable-user-list=true
Remove the compiled dconf configuration for gdm:
$ sudo rm /etc/dconf/db/gdm
Then re-build that database:
$ sudo dconf update
Restart GDM (the easy way) to validate you’ve got this correct:
$ sudo telinit 3 $ sudo telinit 5
Disable Usernames in LightDM (lightdm)
LightDM is much easier than GDM to configure to enforce a user to type in their username as well as their password. Just add/create the following structure to a file called “/etc/lightdm/lightdm.conf”:
[SeatDefaults] greeter-show-manual-login = true greeter-hide-users = true allow-guest = false
Note that is not a typo in the above, it’s actually SeatDefaults, not SetDefaults.
Now just restart lightdm to re-enact that configuration.
$ sudo /etc/init.d/lightdm restart
Disable Usernames in KDM
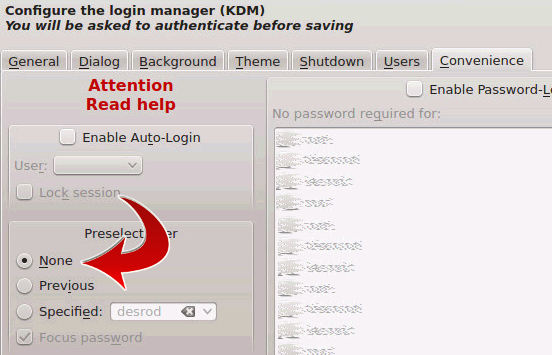
The documentation for KDM claims you can do this with one checkbox in the settings, but that’s not correct. They hide it in two places, which have to be configured. Go to “System Settings” -> “System Administration” -> “Login Screen”. Then on the “Users” tab, adjust the following:
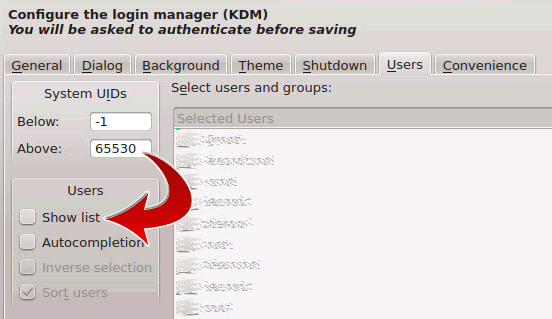
Then on the “Convenience” tab, adjust the following:
Restart your machine, restart kdm or use the runmode 3, 5 trick above, and you should see a screen prompting for a username, but without a userlist visible.
How to disable this on Microsoft Windows (98 through 2008 Server)
- Windows 98 or Me
Open [HKEY_LOCAL_MACHINE\Network\Logon] and create new string value called “DontShowLastUser” and set it to “1” to hide the last user. - Windows 2000 or XP
Open [HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System] and create a new string value, or modify the existing value, called “DontDisplayLastUserName” and set it to “1” to enable or “0” to disable the restriction. - Windows NT
Open [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon] and create a new string value, or modify the existing value, called “DontDisplayLastUserName” and set it to “1” to enable or “0” to disable the restriction.
Now when you get to your login screen, you have to manually, interactively type in your username in order to log in.

 If you’re anything like me, you take security seriously. With all the recent news about the NSA and Prism and over-reach of surveillance, you’ll take this very seriously. I run several layers of nested firewalls, VPNs and other layers of security at my office.
If you’re anything like me, you take security seriously. With all the recent news about the NSA and Prism and over-reach of surveillance, you’ll take this very seriously. I run several layers of nested firewalls, VPNs and other layers of security at my office.