HOWTO: Configure Tor + SASL + irc to connect to Freenode
Tags: freenode, identd, irc, linux, nickname, Perl, Python, Tcl, VMware, xchat
I fought this problem on the train into the city today, because my MiFi‘s hostname was not correctly reversing to it’s given IP (verified by dig) and Freenode was denying the connection; it looked like this:
Mar 22 06:51:41 * Looking up irc.freenode.net Mar 22 06:51:41 * Connecting to chat.freenode.net (86.65.39.15) port 6667... Mar 22 06:51:42 * Connected. Now logging in... Mar 22 06:51:42 * *** Looking up your hostname... Mar 22 06:51:42 * *** Checking Ident Mar 22 06:51:42 * *** Your forward and reverse DNS do not match, ignoring hostname Mar 22 06:51:55 * *** No Ident response Mar 22 06:51:55 * *** Notice -- You need to identify via SASL to use this server Mar 22 06:51:55 * Closing Link: 166.199.4.113 (SASL access only) Mar 22 06:51:55 * Disconnected (Remote host closed socket). Mar 22 06:52:05 Cycling to next server in Freenode... Mar 22 06:52:05 * Disconnected ().
I wanted to connect, to talk to the folks in #linux, and ask them about another question I had (see newer blog post about fullscreen VMware session for that). This was yet another example of the kind of Yak Shaving I deal with on a daily basis.
At first, I tried installing a few identd daemons, then some of the spoofing identd daemons, then purged them all and decided to try identifying using SASL like it suggested.
I did a few seconds of Google’ing and found a helpful website with a SASL plugin in C. I compiled that, installed it into /usr/lib/xchat/plugins, restarted XChat, and attempted to authenticate and identify using this plugin and the instructions.
If the site goes down, I have local copies of the files you need, just email me.
You’ll need to create a file called cap_sasl.conf and put it in ~/.xchat2/, which includes the following syntax:
/sasl [nickname] [password] FreeNode
So if your nickname (username on Freenode) was ‘foobar‘ and your password was “MyS3cretPas5word“, you’d put the following in that file:
/sasl foobar MyS3cretPas5word FreeNode
If you compiled this correctly and put it in the right place, you can also just issue a simple /help sasl command to get the syntax:
Usage: SASL <login> <password> <network>, enable SASL authentication for given network
When you load up XChat, you should see something like this in the main window (if the plugin works):
Python interface loaded Display amarok loaded, type "/disrok help" for a command list Perl interface loaded Tcl plugin for XChat - Version 1.63 Copyright 2002-2005 Daniel P. Stasinski http://www.scriptkitties.com/tclplugin/ Tcl interface loaded Loading cap_sasl.conf Enabled SASL authentication for FreeNode cap_sasl plugin 0.0.4 loaded
The last two lines are what you’re looking for. Now typing “/sasl” will show you the following:
foobar:MyS3cretPas5word at FreeNode
This too, failed to authenticate me and validate my (incorrect) reverse DNS problem. What I saw was this:
Mar 22 20:24:02 * Looking up irc.freenode.net Mar 22 20:24:05 * Connecting to chat.freenode.net (140.211.167.98) port 6667... Mar 22 20:24:05 * Connected. Now logging in... Mar 22 20:24:05 * *** Looking up your hostname... Mar 22 20:24:05 * *** Checking Ident Mar 22 20:24:06 * *** Couldn't look up your hostname Mar 22 20:24:19 * *** No Ident response Mar 22 20:24:52 * Closing Link: 32.138.186.102 (Connection timed out) Mar 22 20:24:52 * Disconnected (Remote host closed socket). Mar 22 20:25:02 Cycling to next server in Freenode...
I decided to investigate a different solution: Tor!
Beware, there are a lot of HOWTO documents and blog posts attempting to describe how to get this working, and literally none of them work from beginning to end (including the one on Freenode itself). I had to go through dozens of these, cherry-picking the right information out and testing many different configuration options until I finally got it to work correctly.
Here’s how I did it…
- First, remove the
cap_sasl.soplugin you might have built (in the above steps) from/usr/lib/xchat/plugins. Leaving it there will just get in the way of the working solution you’re about to implement.$ sudo rm /usr/lib/xchat/plugins/cap_sasl.so
- Install the Tor client on your machine. Since I run Debian and Ubuntu, that was as simple as adding the upstream packge repository URLs to my
/etc/apt/sources.listfile, update, and install the client.If you unlucky enough to have to run a legacy platform like Microsoft Windows, there are instructions on how to do that on the Tor project’s website.
On Linux, just add the tor repositories to your
/etc/apt/sources.listfile and update.deb http://deb.torproject.org/torproject.org lucid main deb-src http://deb.torproject.org/torproject.org lucid main
$ apt-get update && apt-get install tor
That will install and start the Tor client on your machine.
- Next, you need to tell Tor to map it’s internal address to the public “Onion” host. You can do that by adding the following line to the end of your
/etc/tor/torrcfile:# For Freenode IRC mapaddress 10.40.40.40 p4fsi4ockecnea7l.onion
- Now you need to stop/start (or restart) your tor client to reload this configuration (you’re looking for the bolded portion below, to make sure it’s working and parsing the configuration change you’ve added):
$ sudo /etc/init.d/tor restart Stopping tor daemon: tor. Raising maximum number of filedescriptors (ulimit -n) to 32768. Starting tor daemon: tor... Mar 22 20:00:57.573 [notice] Tor v0.2.1.30. This is experimental software. Do not rely on it for strong anonymity. (Running on Linux x86_64) Mar 22 20:00:57.574 [notice] Initialized libevent version 1.4.13-stable using method epoll. Good. Mar 22 20:00:57.574 [notice] Opening Socks listener on 127.0.0.1:9050 done.
Now we have Tor installed, configured, with the Freenode Onion host enabled. Next we have to configure our IRC client to point to our Tor proxy and identify with SASL to connect to the Freenode tor host.
- Load up XChat, and go to Settings → Preferences
- Click “Network setup” on the left side, and enter the information shown here. The important part is that you set the information as:
Hostname: 127.0.0.1 (not localhost) Port: 9050 Proxy type: Socks5 Use proxy for: IRC Server Only
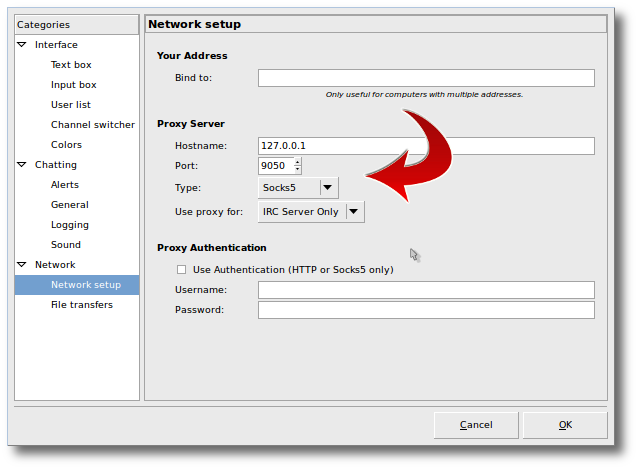
Click “Ok” to save this information
- Now you need to set up a new “network” in XChat for Freenode. Click on the “
XChat” menu in the upper-left of XChat and select “Network List” (or useCtrl-S). You’ll see a window that looks like the following: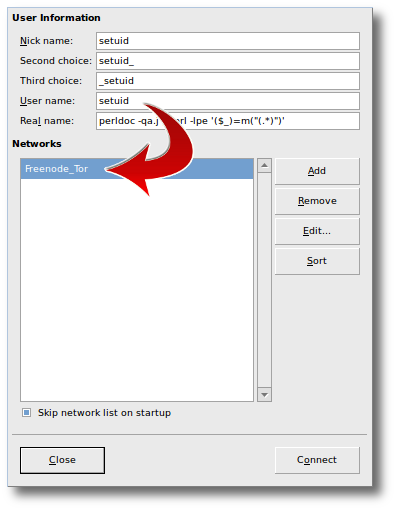
- Once you have that created, click the “
Edit” button on the right-side, and add a new server in that network, using the information here. The server you want to add is “10.40.40.40“: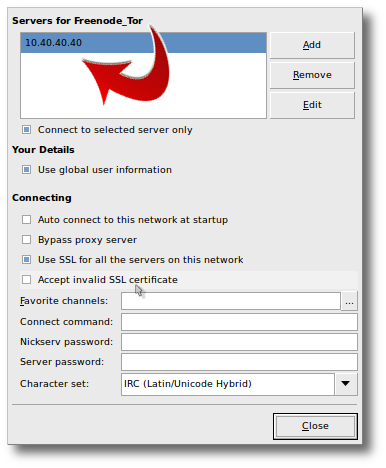
- Now close down XChat and fetch this Perl script from Freenode’s site. In the same directory are several other similar scripts in Perl and Python.
I tried them all, and this one is the only one that worked for me.
Save this script somewhere and move it to your
~/.xchat2/directory and restart XChat. XChat will load up this script automatically. If it does, you’ll see the following output in the status window when you type/sasl:Mar 24 16:52:59 Python interface loaded Mar 24 16:52:59 Display amarok loaded, type "/disrok help" for a command list Mar 24 16:52:59 Perl interface loaded Mar 24 16:52:59 Tcl plugin for XChat - Version 1.63 Mar 24 16:52:59 Copyright 2002-2005 Daniel P. Stasinski Mar 24 16:52:59 http://www.scriptkitties.com/tclplugin/ Mar 24 16:52:59 Tcl interface loaded Mar 24 16:53:06 SASL [action] [action paramters] actions: load reload SASL information from disk save save the current SASL information to disk set set the SASL information for a particular network setdelete delete the SASL information for a particular network delete show display which networks have SASL information set mechanisms display supported mechanisms help show help message - Now you’ll want to configure your authentication, and save it to disk, like this:
/sasl set Freenode_Tor foobar MyS3cretPas5word PLAIN
If you did it right, you’ll see this:
Mar 24 16:57:40 SASL: added freenode_tor: [PLAIN] foobar *
- Now type the following to save the auth to disk:
/sasl save
If that saved correctly, you’ll see:
Mar 24 16:58:05 SASL: auth saved to /home/foobar/.xchat2/sasl.auth
You’re almost done!
- Now launch XChat if you haven’t already, and select your “
Freenode_Tor” network from the list, and click “Connect” on the lower-right. This will now attempt to connect to “10.40.40.40” through your Tor proxy (running on127.0.0.1on port9050), and present the cached SASL auth to chat.freenode.net when it connects. It will look like this:Mar 24 17:00:50 Python interface loaded Mar 24 17:00:50 Display amarok loaded, type "/disrok help" for a command list Mar 24 17:00:50 SASL: auth loaded from /home/foobar/.xchat2/sasl.auth Mar 24 17:00:50 Perl interface loaded Mar 24 17:00:50 Tcl plugin for XChat - Version 1.63 Mar 24 17:00:50 Copyright 2002-2005 Daniel P. Stasinski Mar 24 17:00:50 http://www.scriptkitties.com/tclplugin/ Mar 24 17:00:50 Tcl interface loaded Mar 24 17:02:33 * Looking up 10.40.40.40 Mar 24 17:02:33 * Looking up 127.0.0.1 Mar 24 17:02:33 * Connecting to 127.0.0.1 (127.0.0.1) port 9050... Mar 24 17:02:47 * * Certification info: Mar 24 17:02:47 * Subject: Mar 24 17:02:47 * OU=Domain Control Validated Mar 24 17:02:47 * OU=Gandi Standard Wildcard SSL Mar 24 17:02:47 * CN=*.freenode.net Mar 24 17:02:47 * Issuer: Mar 24 17:02:47 * C=FR Mar 24 17:02:47 * O=GANDI SAS Mar 24 17:02:47 * CN=Gandi Standard SSL CA Mar 24 17:02:47 * Public key algorithm: rsaEncryption (2048 bits) Mar 24 17:02:47 * Sign algorithm sha1WithRSAEncryption Mar 24 17:02:47 * Valid since Jan 14 00:00:00 2011 GMT to Jan 14 23:59:59 2012 GMT Mar 24 17:02:47 * * Cipher info: Mar 24 17:02:47 * Version: TLSv1/SSLv3, cipher DHE-RSA-AES256-SHA (256 bits) Mar 24 17:02:47 * Connected. Now logging in... Mar 24 17:02:47 * *** Looking up your hostname... Mar 24 17:02:47 * *** Checking Ident Mar 24 17:02:47 * *** Got Ident response Mar 24 17:02:47 * *** Couldn't look up your hostname Mar 24 17:02:48 CLICAP: supported by server: identify-msg multi-prefix sasl Mar 24 17:02:48 CLICAP: requesting: multi-prefix sasl identify-msg Mar 24 17:02:49 CLICAP: now enabled: multi-prefix sasl identify-msg Mar 24 17:02:51 You are now logged in as foobar. Mar 24 17:02:53 * *** Spoofing your IP
Now you’re connected to Freenode through Tor. You can verify this by issuing the following:
/whois foobar * [foobar] (debian-tor@gateway/tor-sasl/foobar): perldoc -qa.j | perl -lpe '($_)=m("(.*)")' * [foobar] anthony.freenode.net :Irvine, CA, USA * [foobar] is using a secure connection * [foobar] is connecting from *@gateway/tor-sasl/foobar 255.255.255.255 * [foobar] idle 00:02:09, signon: Thu Mar 24 17:02:53 * [foobar] is logged in as foobar * [foobar] End of WHOIS list.
I called mine Freenode_Tor here. Remember the name and how you spelled it here, this is important.
Click “Close” to save this information.
Welcome to a more-secure, more-anonymous way to chat with your friends, colleagues and the community.
NOTE: As I type this, I am one of 3 total people on all of Freenode, using Tor, out of 69,725 total users on the network.
* 1095 8451 :Current local users 1095, max 8451 * 69725 71006 :Current global users 69725, max 71006

Ruby said on June 4th, 2011 at 8:59 pm quote
This tutorial was super helpful. Thank you!
In0cula said on July 22nd, 2011 at 4:41 pm quote
thanx man, it works!!
Ed said on October 8th, 2011 at 3:59 pm quote
The latest gentoo builds an xchat without perl support. Make sure your package.use file has net-irc/xchat perl or perl is in your make.conf
lucio said on October 14th, 2011 at 6:10 pm quote
this guide is very good, work like a sharm, thank you very much
Anonymous said on January 5th, 2012 at 12:26 am quote
Thanx bud worked perfectly :-)
null said on November 28th, 2012 at 2:21 am quote
when i run /sasl save i get unknown cmd and i dont have it defined as a cmd ??? i cant progress to connect… ?
Plugin defined commands:
UNLOAD LOAD RELOADALL SOURCE TCL
SASL UNLOAD LOAD PY RELOADALL
UNLOADALL PL_RELOAD RELOAD UNLOAD LOAD
TIMER
Type /HELP for more information, or /HELP -l
/home/shmick
Updated SASL settings for network Freenode-tor
Unknown Command. Try /help
Usage: /SASL <-set|-unset> [ ]
Unknown Command. Try /help
Ryan said on December 9th, 2012 at 11:08 am quote
Can I just say that you are the absolute best, EVER!?
Thank you so, so much for this. I can finally enjoy participating on Freenode without feeling as unsafe as I used to. You absolutely, totally rock dude.
Thanks again!
Wilson said on April 30th, 2013 at 5:51 pm quote
Thanks! Worked great!
Quick note: In order to make this work, you must be using a registered nick. At least, that was the problem I was experiencing.
Thanks again!